Cybersecurity
While the Australian Cyber Security Centre’s Essential 8 framework represents a good baseline for improving your businesses security posture – we felt it needed more.
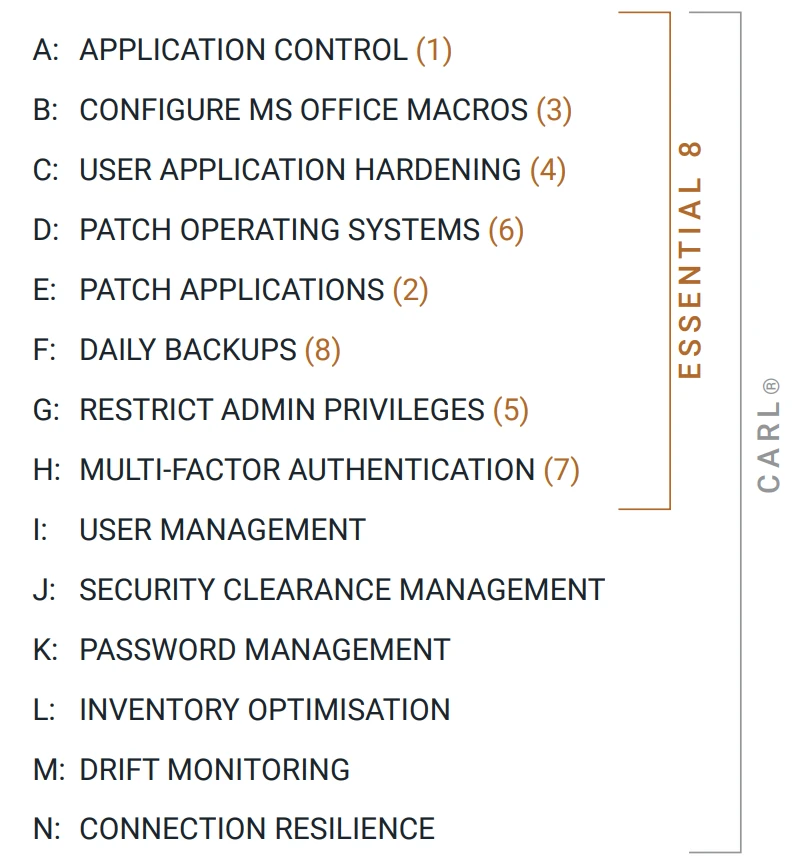
In developing C.A.R.L.® (Monocera’s Cybersecurity and Resillience Lifecycle) we considered the Essential 8, NIST, and CIS Frameworks, then added 6 more metrics we felt were equally important for SME’s.
In 2023, the average financial loss to SME’s was $88,407 per reported incident. We can audit, protect and maintain C.A.R.L.® maturity for a fraction of this while allowing you to rest easy knowing your environment is protected.
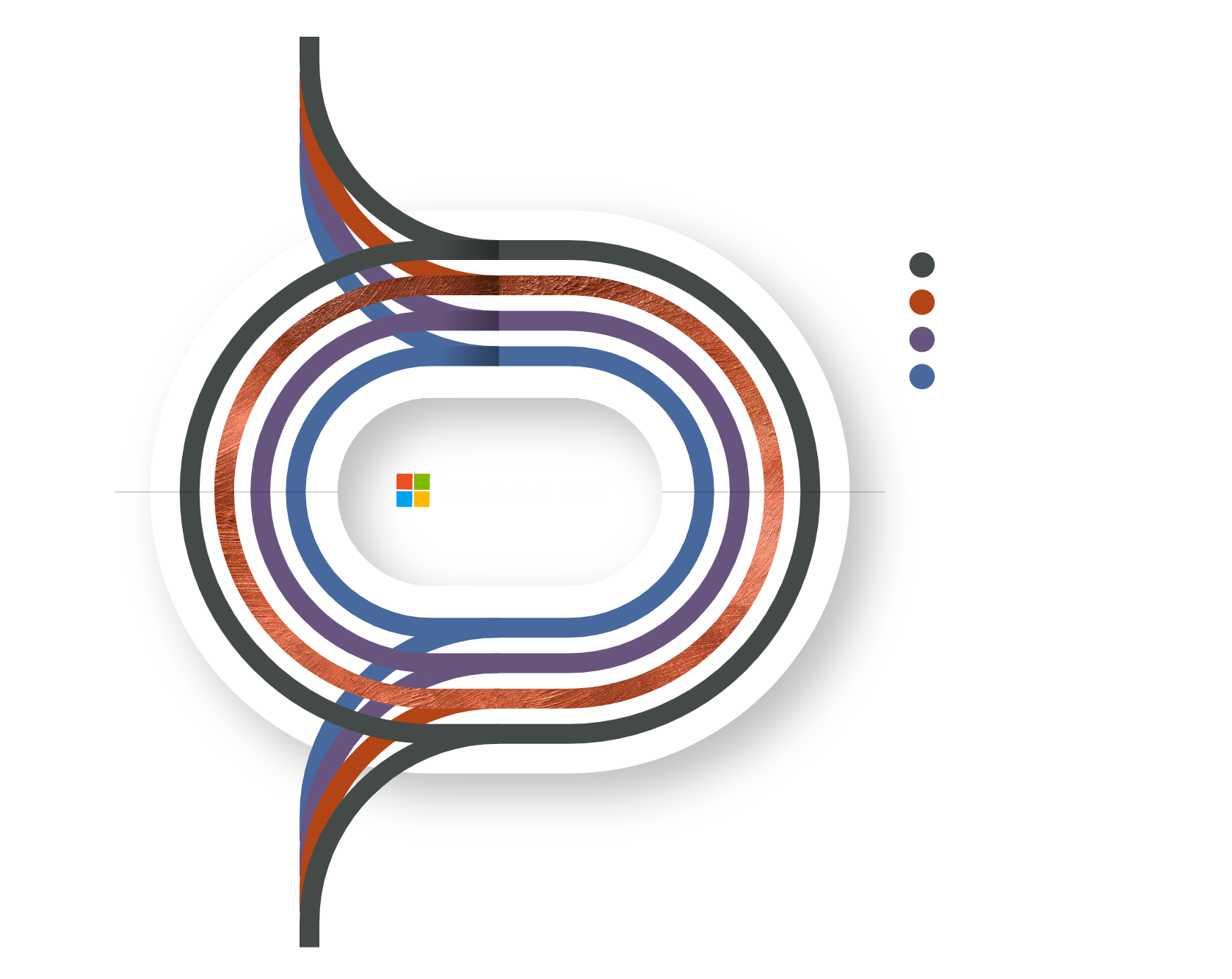
Monocera® clients benefit from ourecosystem. Our Cybersecurity and Resilience Lifecycle.

Modern cybersecurity is much more complex than up-to-date antivirus and good password hygiene. To effectively protect your business and IT ecosystem you must consider threats and problems beyond just malicious attackers. This requires system and application security, system resilience, monitoring and contiual review and updates.
Let us introduce you to C.A.R.L® (Cybersecurity And Resilience Lifecycle).



Monocera’s premium Managed Service clients benefit from our C.A.R.L® ecosystem. Our cybersecurity and resilience lifecycle system.
In creating C.A.R.L.® we began with the Australian Cyber Security Centre’s Essential 8 and the CIS and NIST International standards and then went on to create a more robust and resilient system for protecting your IT infrastructure, and your business.
Of course, every business is different and has different levels of risk, data sensitivity, system reliance and commercial capability.
The Essential Eight
(Australian Cyber Security Centre)
The Essential Eight are a core set of risk mitigation strategies for a base level of effective cybersecurity on Microsoft Windows-based internet connected networks. It also establishes levels of ‘maturity’ which measure the depth of adoption of these strategies.
CIS Benchmarks
The CIS provides internationally benchmarked configuration standards for the applications within your ecosystem. It hardens and protects the applications and security associated with them while also allowing organisations to demonstrate compiance with regulations, frameworks and procurement requirements.
NIST Cybersecurity Framework
(National Institute of Standards and Technology)
NIST provides a process framework to identify, assess, and manage cyber risks. It facilitates prioritisation and implementation of policy, process and technological approaches to managing those risks.
The core C.A.R.L.® service provides a high level of risk mitigation and resilience while minimising administration requirements.
It’s a System – Lifecycle
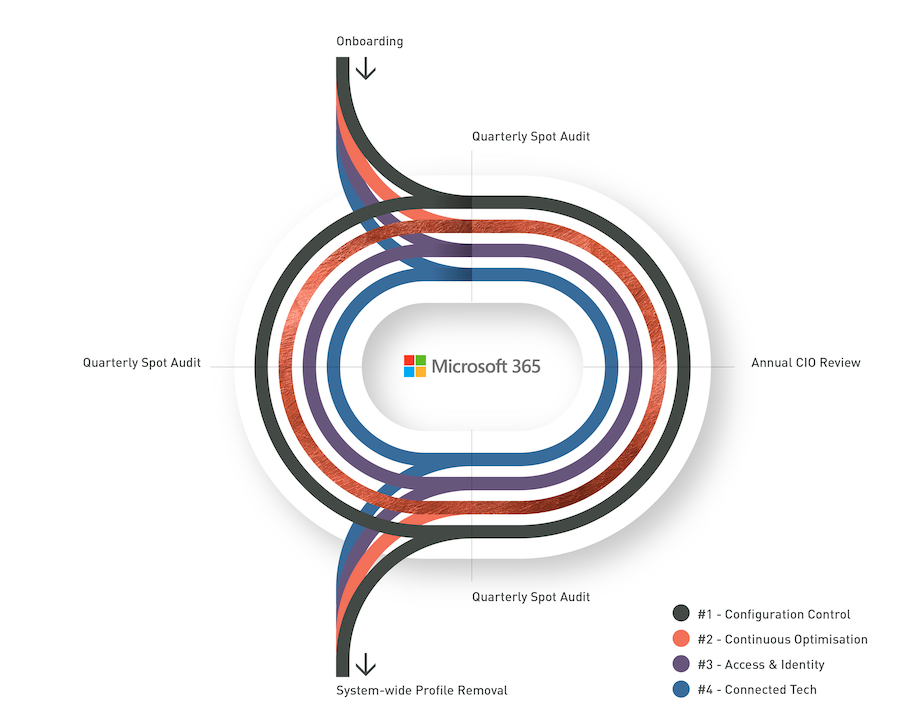
Effecive cybersecurity and IT Ecosystem resilience requires constant and continual attention. The Monocera C.A.R.L.® process incorporates cutting edge monitoring and automation to track, protect and report on system health.
Quartlerly Spot Audits are carried out by Monocera technicians testing existing system, trialing recovery processes and looking for optimisation opportunities. These are coupled with an Annual CIO Review meeting to assess performance and confirm requirements for the coming year.
Staff and technology onboarding and exit management are also very important, and an often overlooked or underdone part of the IT ecosystem. Done correctly these processes improve performance and minimise risk.
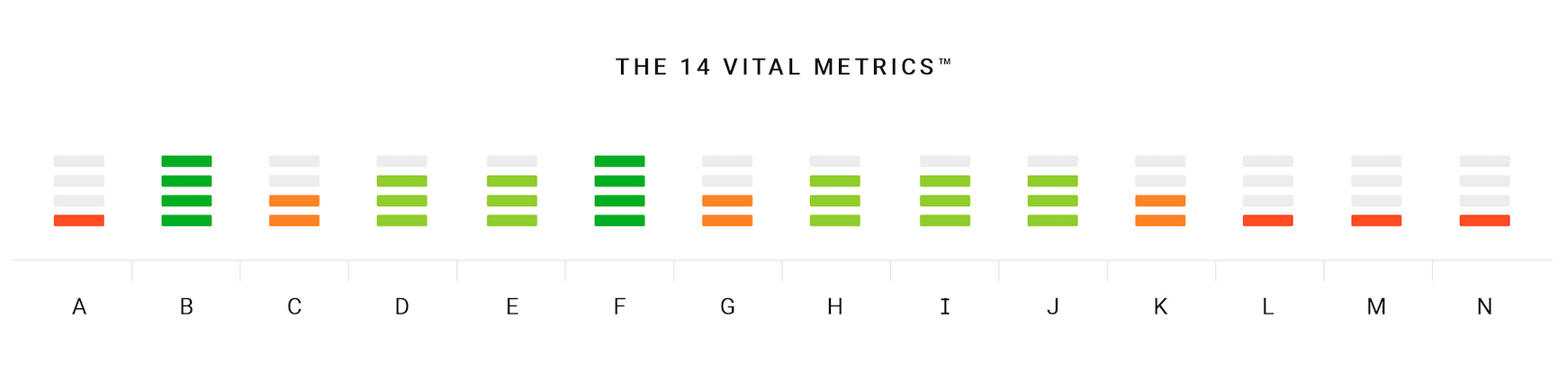
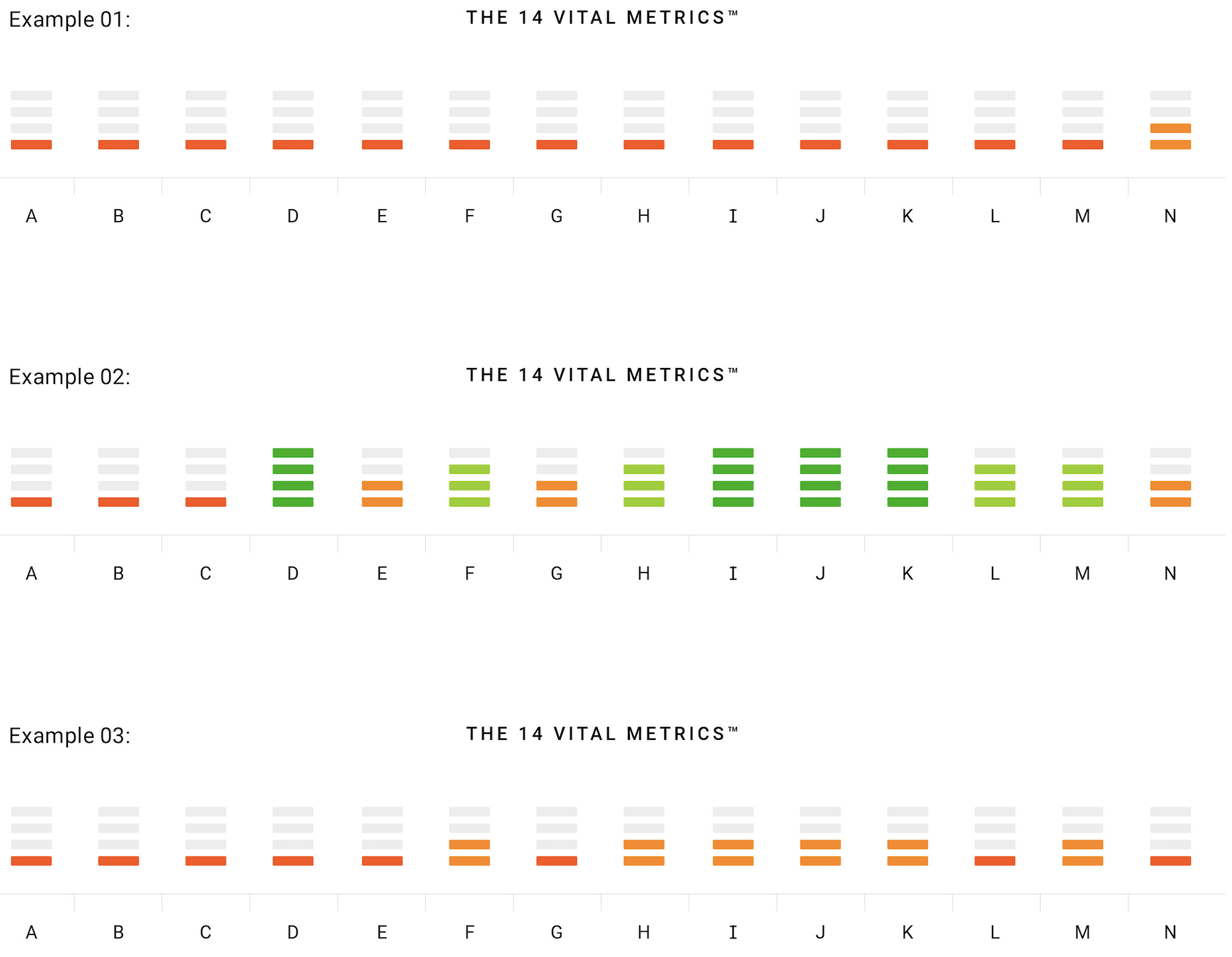
C.A.R.L® Health Bar™

Let us check your pulse
Our C.A.R.L.® assessment tools allow us to measure an organisations cybersecurity and IT resilience strategies effectively and in-depth. The health bar delivers a summary of those findings across the four core diagnostics.

Configuration Control
#1
The overall configuration of all system applications including protective security apps and systems.
A – APPLICATION CONTROL (1)
B – CONFIGURE MS OFFICE MACROS (3)
C – USER APPLICATION HARDENING (4)
Continuous Optimisation
#2
The continuous monitoring and updating of operating systems, applications, back-up systems, processes and procedures.
D – APPLICATION CONTROL (1)
E – CONFIGURE MS OFFICE MACROS (3)
F – USER APPLICATION HARDENING (4)
Access & Identity
#3
Management of user identity, access, administration and security privileges including identity validation and authentication.
G – RESTRICT ADMIN PRIVILEGES (5)
H – MULTI-FACTOR AUTHENTICATION
I – USER MANAGEMENT
J – SECURITY CLEARANCE MGMT
K – PASSWORD MGMT
Connected Tech
#4
The management and optimisation of all elements of the IT ecosystems hardware and connections between that hardware to each other and cloud infrastructure.
L – INVENTORY OPTIMISATION
M – CLOUD MONITORING
N – CONNECTION RESILIENCE
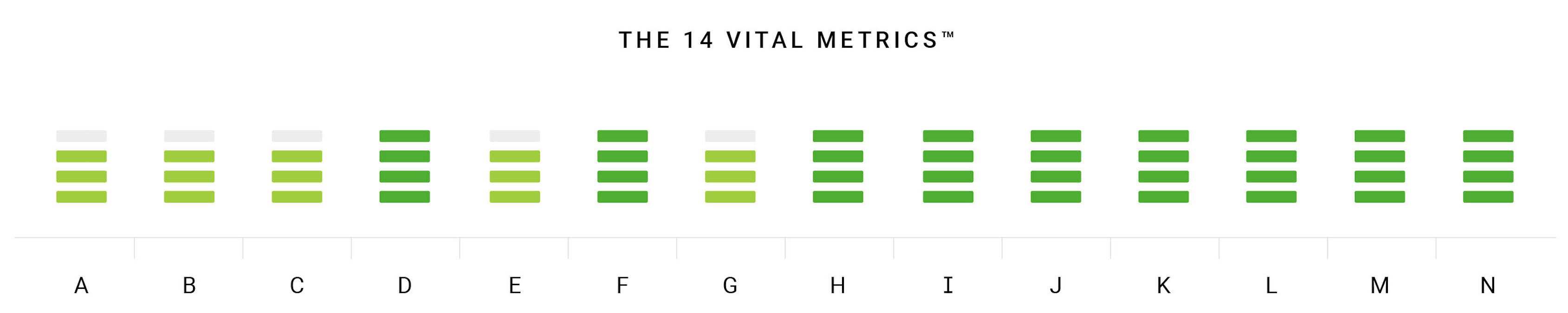
Going Deep
A full C.A.R.L.® Audit assess an oranisation’s current cybersecurity and resilience position.
It identifies weaknesses and vulnerabilities which can be addressed.
By implementing a Monocera C.A.R.L.® program these metrics will be raised to a level of industry best practice or beyond.
Latest Intelligence
How to Spot a Dodgy Website
As anyone with a mobile phone in Australia knows, scams are on the rise. Whether it’s “mum” asking you send through a couple hundred bucks on loan for groceries, or “Linkt” asking you to top up your toll account, sometimes fraudulent and scammy characters can be hard...
Chrome Coming to End of Life for Windows 7 & 8
Late last year, Google announced that Chrome will no longer be supported on Windows 7 or Windows 8/8.1. Their newest version of Chrome (Chrome 110) is set to be released on February 7th. This newest version will be the first to require you running Windows 10 or...
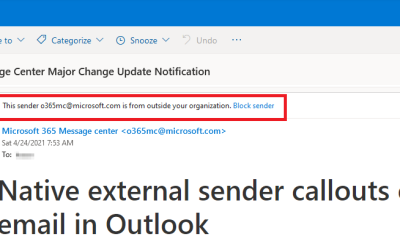
Why You Should Keep Outlook’s New External Email Warning Tag
We’ve recently had several clients come to us asking to remove the external email warning tag on their business’ Microsoft Outlook. Our guidance, however, is that tag should be kept as its benefits far outweigh the cons. Let’s run through why. What is the external...